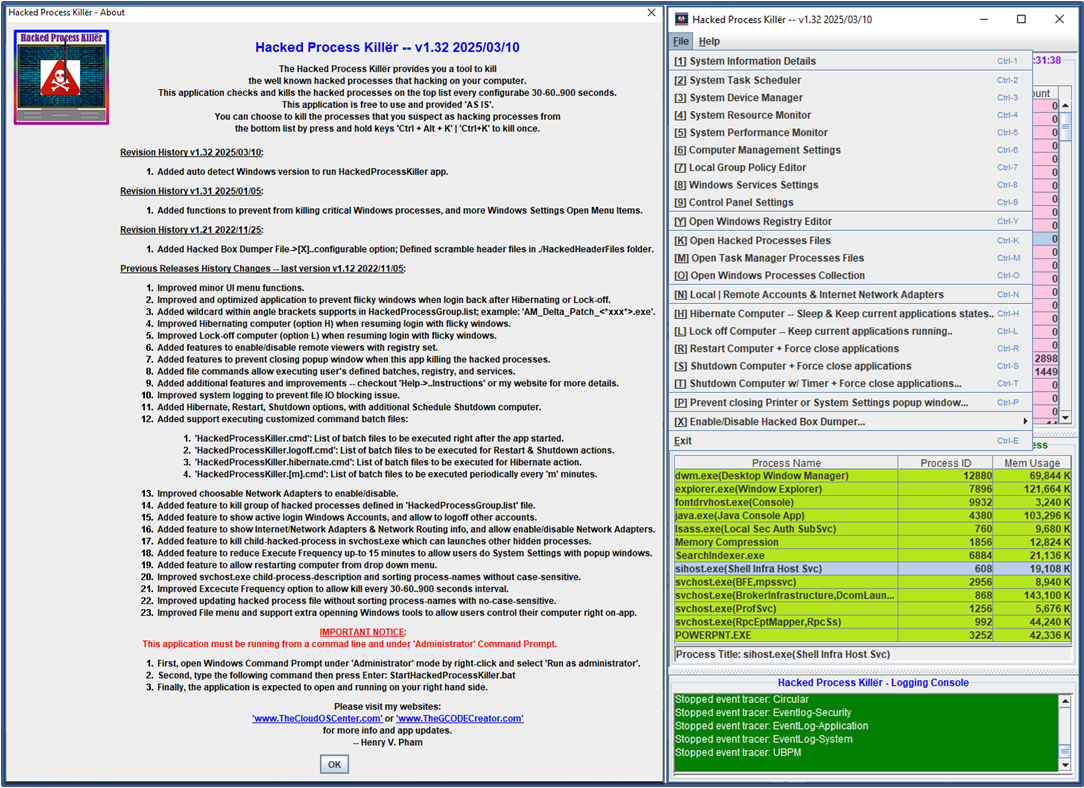
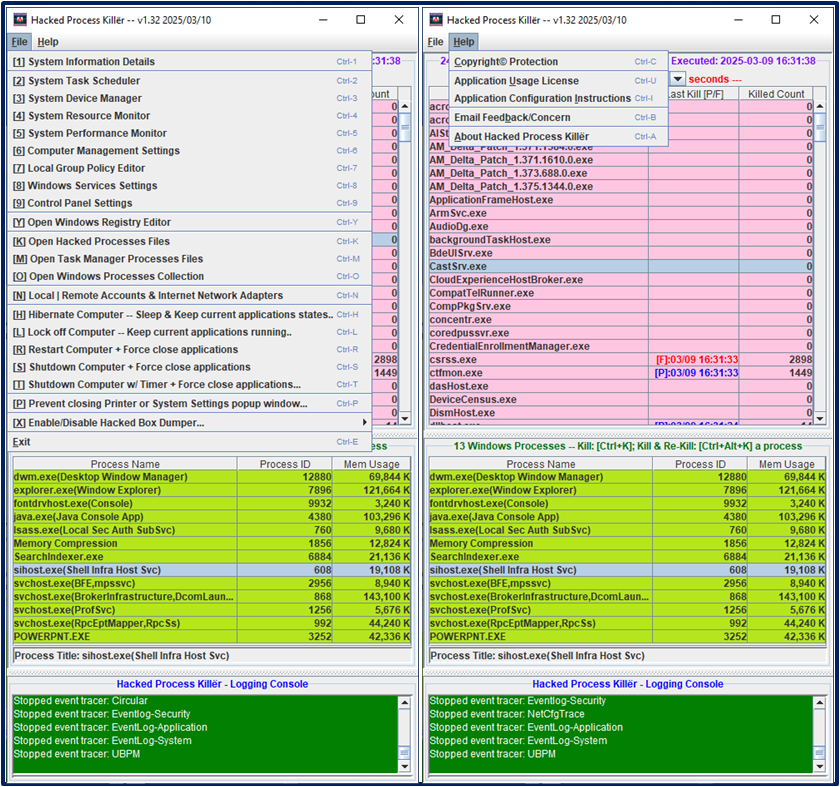
|
Secure Windows Folder Tricks (same as Windows 10)
- How to create and take ownership of a folder? The above steps you already have the batch file 'W10TakeOwnerFolder.bat'. Create and/or take ownership of 'C:\W10-SECURED-DATA-FOLDER' for instance, you can use command prompt 'C:\W10-SECURED-SW-FOLDER\HackedProcessKiller\W10TakeOwnerFolder.bat "C:\MY W10 SECURED DATA FOLDER"'. The batch script will create folder 'C:\MY W10 SECURED DATA FOLDER' if it does not exist.
- How to check for folder ownership? You can try the followings with snapshots.
- Select and right-click a folder, select 'Properties' then a window will popup.
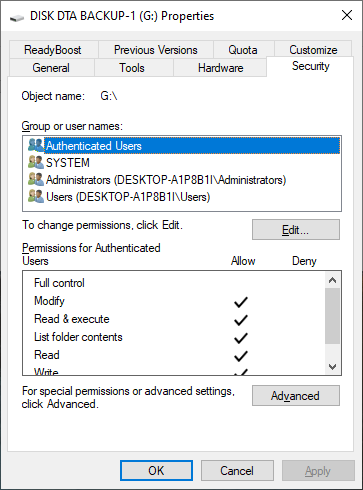
- From Security tab, click 'Advanced' button.
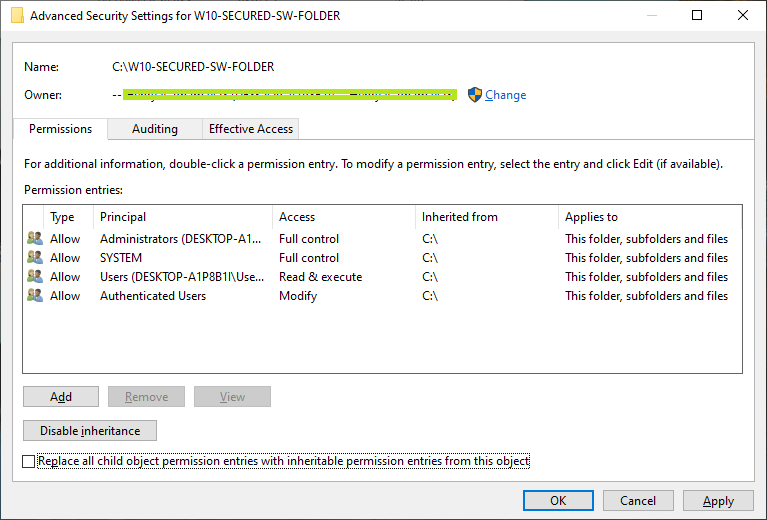
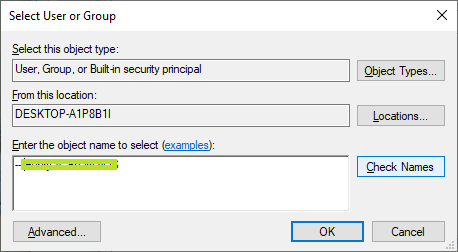
- Click 'Change' link and enter your account name to change ownership if it's not your account. Click 'Check Names' to make sure your account is correct, then click 'OK' button to confirm.
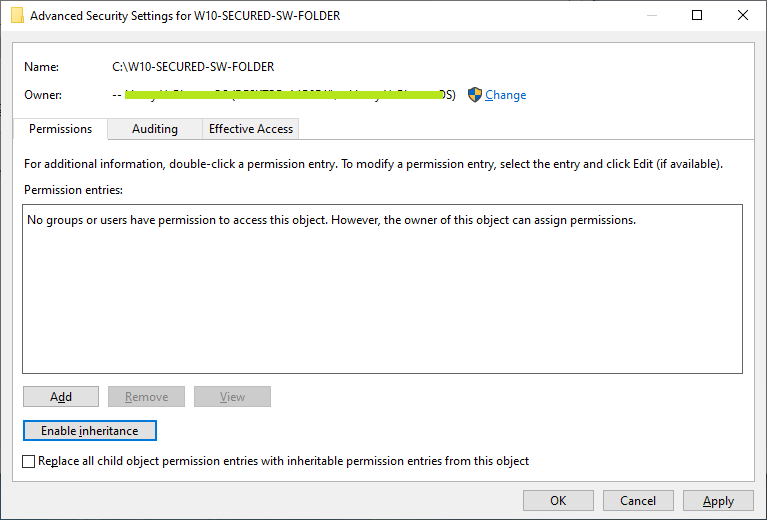
- Next, make sure delete other accounts before add your account into the folder permission box by click on 'Remove' button or 'Disable Inheritance' button.
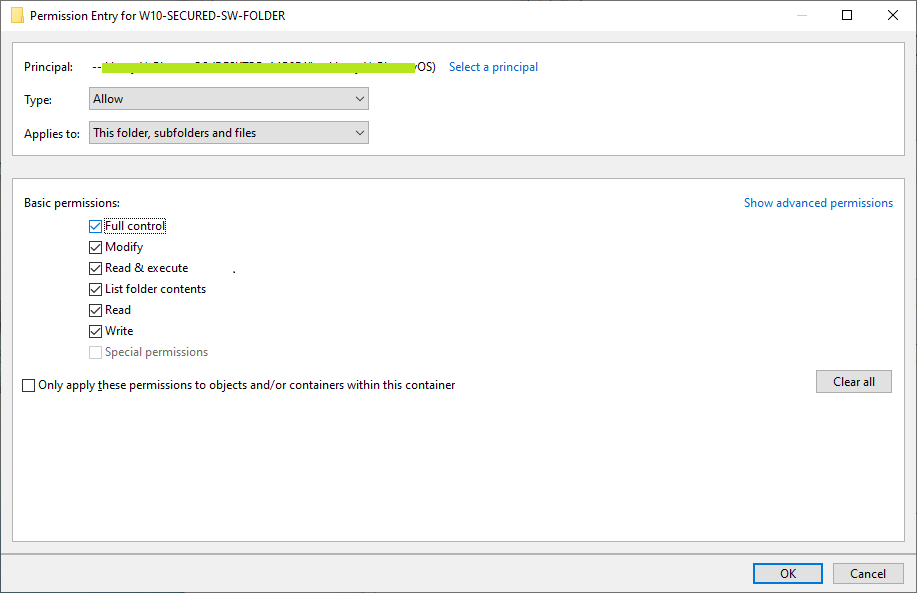
- Then, click 'Add' button to add your account name as a principle account, and click 'OK' to confirm. Note that the popup window will be the same as shown in step 3.
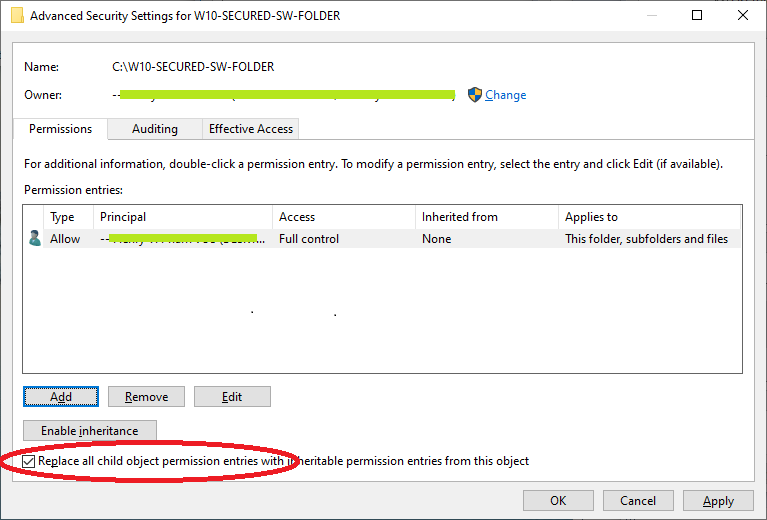
- Now make sure to check 'Full Control' permissions as shown below.
- Finally, you have full permission for your folder as shown. Important: Make sure the check 'Replace all child object permission...' before click 'OK' button.
Secure USB Drive Tricks (same as Windows 10)
- How to set ownership for your USB stick/drive? You can try the followings with snapshots.
- First, select and right-click on USB drive, and select 'Properties' then a popup window will be shown.
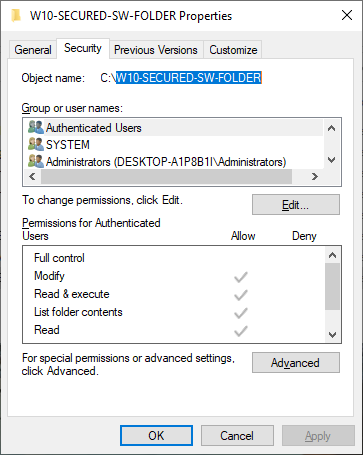
- From Security tab, click 'Advanced' button. A popup window will show as below.
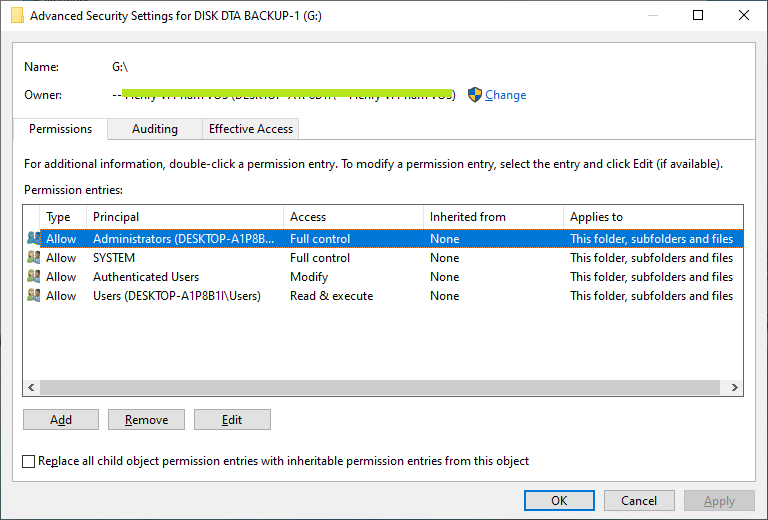
- Click 'Change' link and enter your account name to change ownership if it's not your account. Click 'Check Names' to make sure your account is correct, then click 'OK' button to confirm.

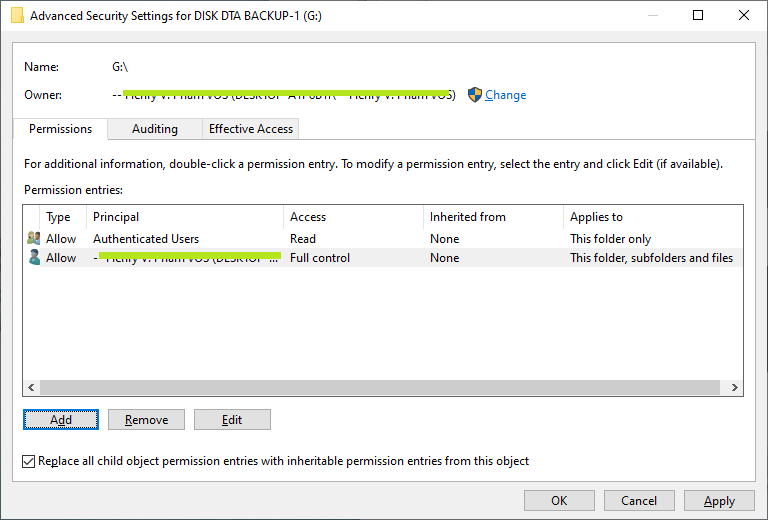
- Next, make sure delete other accounts (keep only 'Authenticated users' account) before add your account into the folder permission box by click on 'Remove' button or 'Disable Inheritance' button.
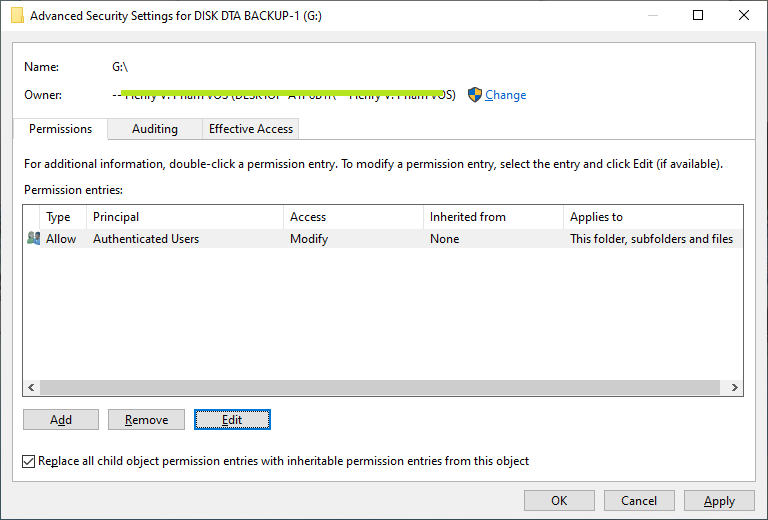
- Then, click 'Modify' button to change permission of the 'Authenticated users' account to 'Read' readonly and 'Applies to: This folder only' as shown below.
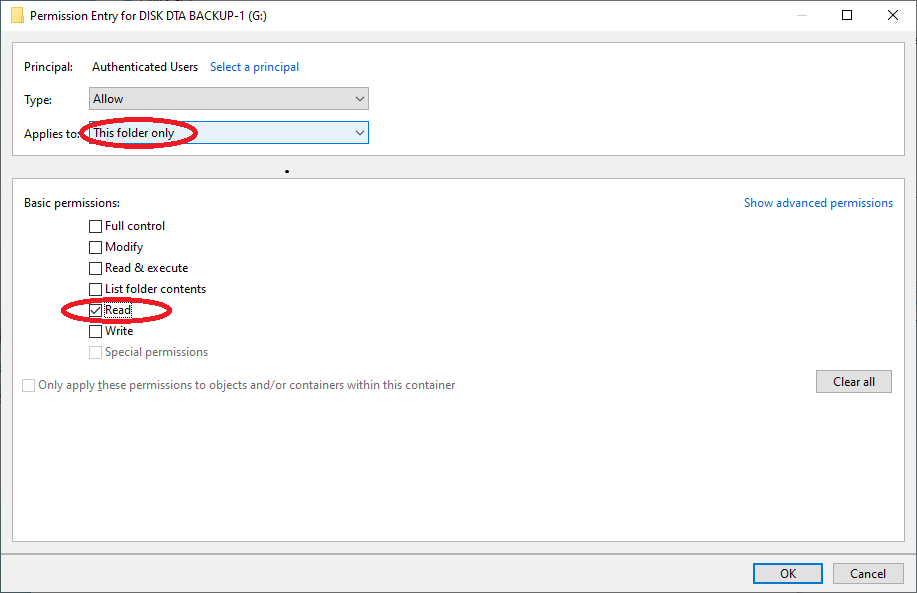
- Now add your account as a principle account with 'Full Control' as shown below.
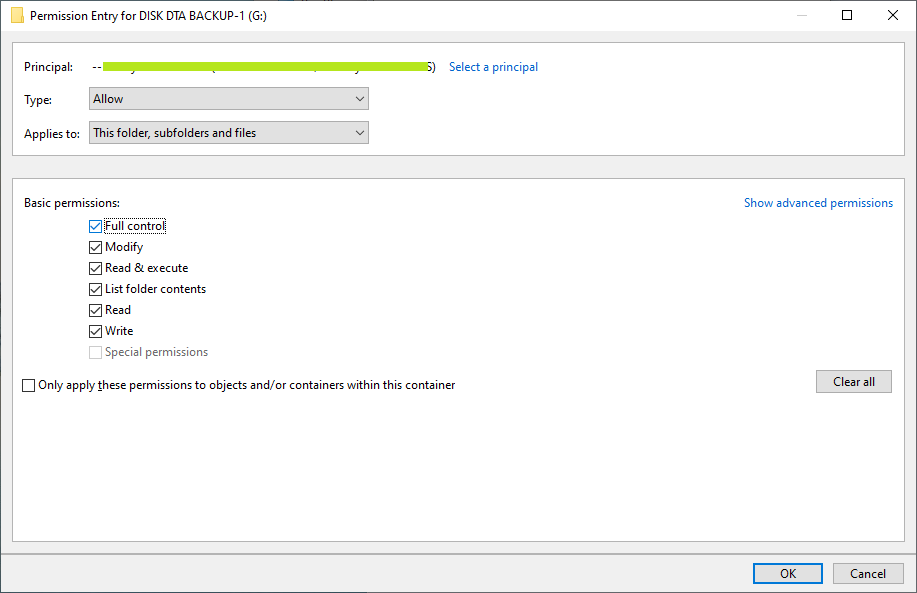
- Finally, you have full permission for your folder as shown. Important: Make sure the check 'Replace all child object permission...' before click 'OK' button.
Take Ownership of USB Drive Tricks (same as Windows 10)
- What happens if you put your USB drive to a different Windows PC? You cannot able to access to your folders/files. You need to set ownership for your USB stick/drive to gain access. You can try the followings with snapshots.
- How to take ownership of a USB drive? The above steps you already have the batch file 'W10TakeOwnerFolder.bat'. You can take ownership of USB drive 'E:' for instance, you can use command prompt 'C:\W10-SECURED-SW-FOLDER\HackedProcessKiller\W10TakeOwnerFolder.bat "E:"'. The batch script will set your ownership to the USB drive.
- How to take ownership of a USB drive manually? You can try the followings with snapshots.
- First, select and right-click on USB drive, and select 'Properties' then a popup window will be shown with a strange account 'S-1-5-21-...'.
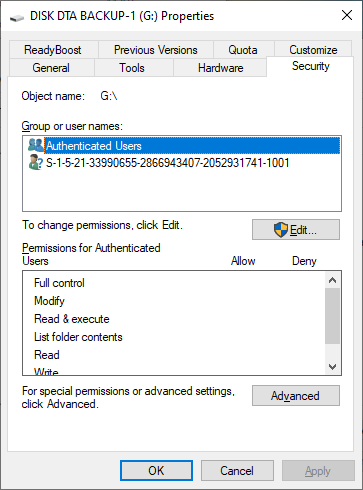
- From Security tab, click 'Advanced' button. A popup window will show as below.
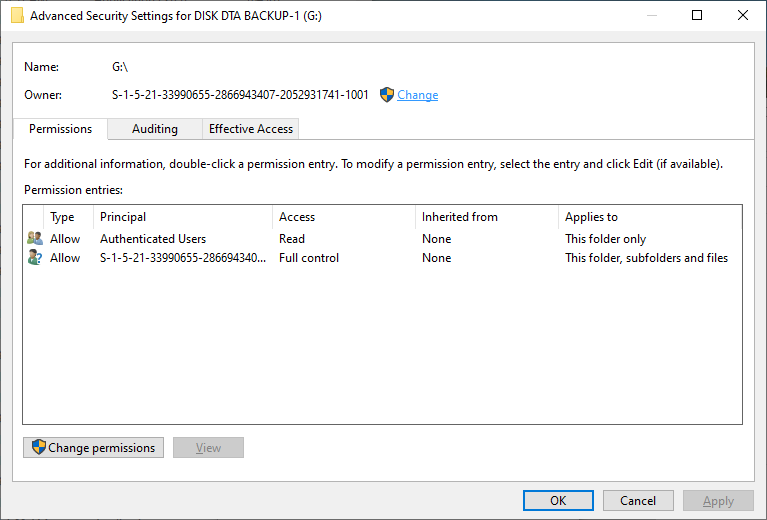
- Click 'Change' link and enter your account name to change ownership if it's not your account. Click 'Check Names' to make sure your account is correct, then click 'OK' button to confirm.
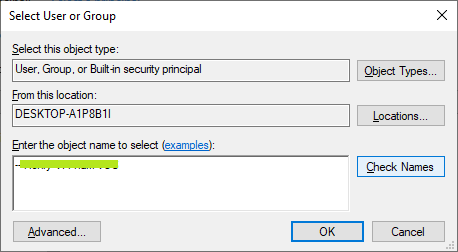
- Then, make sure permission of the 'Authenticated users' account to 'Read' readonly and 'Applies to: This folder only' as shown below.

- Now add your account as a principle account with 'Full Control' as shown below.

- Finally, add your account as a principle account with 'Full Control' for full permission for your folder as shown. Important: Make sure the check 'Replace all child object permission...' before click 'OK' button.

- Your USB drive is now on your own account. However, you need to remember to take ownership of your USB drive when you switch to different Windows PC.
- These steps can be use to get back your data from your crashed Windows PC!
|
|